Unauthenticated SSH to Console Ports
Configure > Services > SSH
The Unauthenticated SSH Access feature provides the option to access console ports (using TCP high ports) by establishing per-port SSH connection between a console and serial ports at a remote device. This allows a single step log-in and avoids the necessity for two log-ins to reach a remote end device within secure, closed networks.
Usually, you would need to authenticate on the Opengear appliance, followed by any log in to a device you are connecting to via the serial port.
When unauthenticated access is enabled SSH is available to all serial ports on the device without requiring a password.
Note: Unauthenticated access can be used with or without IP aliases for serial ports.
Caution: For security, Unauthenticated SSH should only be used when operating within a trusted, closed network, for example within a lab. There is a security risk in allowing any kind of unauthenticated access to serial ports and any terminals connected to them.
Enable Unauthenticated SSH
Authenticated or Unauthenticated access is determined via a global configuration option. Unauthenticated access to individual ports is achieved by command such as ssh -p 300X user@<IP>.
Enable SSH
Note: This feature may be enabled using the default settings without the need for configuration.
- Open the SSH form, Configure > Services > SSH > SSH (form).
- Complete the SSH form (if this is the first time Unauthenticated SSH has been used), a description of the input data is provided at Properties and Settings in this topic.
- When required, enable the Unauthenticated SSH feature by clicking the Enabled button.
Note: Unauthenticated access to all serial ports will be available through SSH on TCP port 3000+ or Serial Port IP aliases.
Enable/Disable
Enabling or disabling this feature is done in the user interface.
To enable the feature click on the Enabled button then click the Apply button. The feature is enabled immediately and a pop-up will confirm that the feature is enabled.
Note: Clicking the Apply button saves any changes you have made to the SSH form. A Details Saved banner confirms that the changes have been saved.
To disable the feature click on the Disabled button then click the Apply button. There is no confirmation pop-up when the feature is disabled.
Connecting Directly to Serial Ports
For ports that have been configured with the SSH access service, you can connect directly to a port and start a session, bypassing the chooser, by using one of the four conventions described in the following:
| Convention | Example |
|---|---|
|
Use a network client to connect to the service network Base Port + serial port number. |
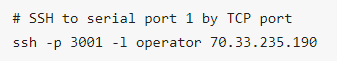
In this example, the SSH base port is TCP port 3000, so SSH to TCP port 3001 directly connects you to serial port 1 |
|
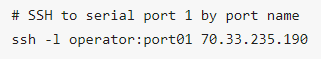
SSH to the Opengear device, log in adding :portXX to your username (e.g. root:port01 or operator:port01) |
|
|
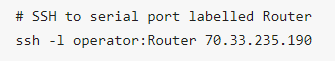
SSH to the Opengear device, log in adding the :port-label to your username (e.g. root:Router or operator:Router) |
|
| Configure per-port IP aliases |
Note: For additional reading on connecting to serial ports see:
https://opengear.zendesk.com/hc/en-us/articles/216373543-Communicating-with-serial-port-connected-devices
Note: Serial ports in the Local Console and Disabled ports modes are not available for SSH connection.
Feature Persist
If the device has an active console session after closing pmshell, connecting to the device again will resume the session and you are not prompted for the device password.
Properties and Settings
| Property | Definition/Range |
|---|---|
| Serial Port Delimiter |
A character that separates the User name and port selection information. The default value is the + character. Default is ‘+’, maximum length is 1. The prohibited characters are ‘\’, ‘ ” ’, ‘ ` ’, ‘ ‘, ‘=’ and ‘#’. Source: schema required ssh_delimiter: string (default = "+"; minimum = 1; maximum = 1; validator = ("ssh_url_delimiter")), Source: validator if (strlen(v) != 1) valid = 0; else if (v[0] == '\'') valid = 0; else if (v[0] == '"') valid = 0; else if (v[0] == '`') valid = 0; else if (v[0] == ' ') valid = 0; // breaks sshd_config else if (v[0] == '=') valid = 0; // breaks sshd_config else if (v[0] == '#') valid = 0; // breaks sshd_config else if (!isprint(v[0])) valid = 0; else { valid = 1; } |
| Port Number for Direct SSH Links |
This port number will be used for direct SSH links on the serial ports page. Set this option if you have configured SSH to be reachable on a non-standard port. |
| Max Startups Start |
The number of connections pending authentication before new connections begin to be refused. Required start: int (minimum = 1; default = 10) |
| Max Startups Full |
The number of connections pending authentication before all new connections are refused. Required full: int (minimum = 1; default = 100) |
| Max Startups Rate |
This is the percentage rate at which new connections are refused once the Max Startups value is reached. The rate is increased to 100% at Max Startup Full. Required rate: int (minimum = 1; maximum = 100; default = 30), The rate at which connections are refused randomly begins at max startup rate and increases linearly until the number of connections pending authentication reach max startups full, in which case 100% of new connections are refused. |
| Unauthenticated Access to Serial Ports | This is the feature Enable/Disable button. |