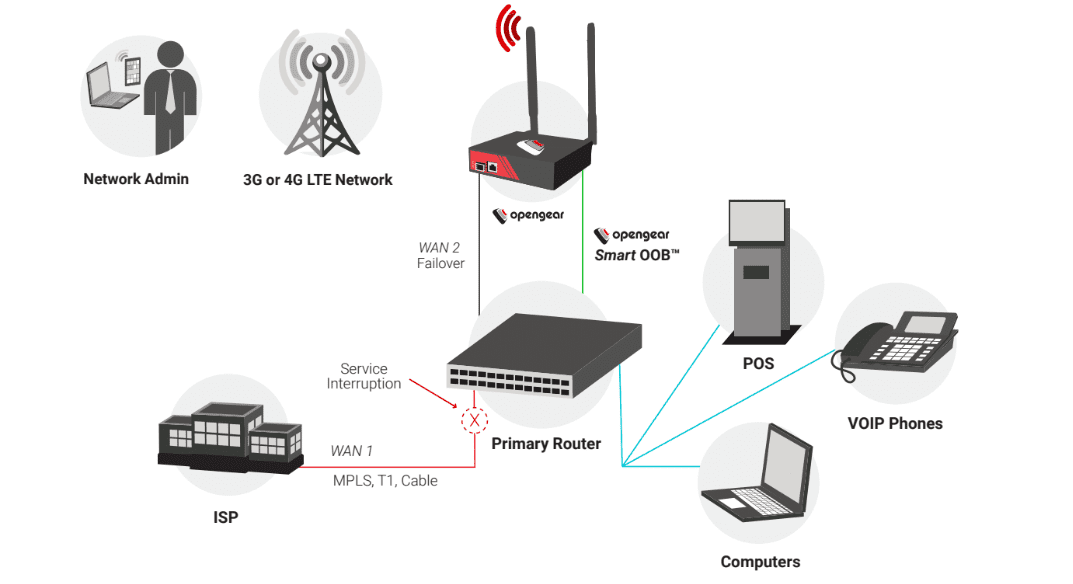
Console servers with internal cellular modems give you a wireless broadband IP connection for high-speed access to your remote sites. And Opengear Failover to Cellular™ provides continued Internet connectivity for remote LANs and equipment over high-speed 4G LTE or 3G networks when the primary Internet link is unavailable. While cellular wireless gives you great flexibility and availability, you need to make sure that you address potential security weaknesses from the start.
Here’s a brief look at the vulnerabilities and practical steps you can take to mitigate your risks. For more detailed suggestions, download our Whitepaper, Keeping Your Cellular Modem Secure.
Require VPN Connections
When your cellular IP address is publicly available, typing that IP address in a browser gives you password protected access to a remote cellular modem. While this remote access is convenient, it is also available to an attacker.
The best option is to avoid using a publicly available cellular modem IP. If you can, restrict inbound connections to a VPN client to secure remote access. Access to the IP is only available through an authenticated and encrypted network tunnel. And if the VPN is configured with strong keys and ciphers, it will be virtually uncrackable. The trade-off is that that you lose the convenience and minimal configuration of direct SSH, and that a VPN client has to be configured at each remote access location. If that’s not feasible, there are other steps you can take to decrease exposure.
Disable Wireless When It’s Not Needed
You can keep your public cellular connection enabled only when you need it. Your Opengear device can automatically turn the cellular connection on when failover occurs and off when the issue is resolved. The cellular connection is completely inactive during normal operation. This keeps the interface off the Internet as much as possible to both avoid high data charges and lessen exposure of this potential target from malicious actors.
Use Strong Passwords
When your IP is public, the username and password is the only thing protecting it from malicious actors. Make sure you configure an admin group account and require strong passwords. Also enable brute force protection (fail2ban) for the cellular IP which limits the number of authentication attempts a user can make before a temporary ban is put in place.
Tighten Up Your Firewall
Lock down the firewall. Start with more restrictions than you think you’ll need. You should disable ping responses to thwart ping sweeps of public address space by attackers seeking targets. Disable unencrypted or insecure services and limit listening ports.
Consider running services on alternate ports to provide some degree of security by obscurity against attacks specifically targeting ports 22 and 443. And whenever possible, restrict access to trusted source networks only. If you have a known range of addresses, block all connections originating from other networks.
Monitor Your Data Usage
Finally, keep an eye on your data usage. Runaway data usage may indicate, among other things, a malicious worm script, so you need to monitor data usage in as many ways possible.
Feel secure in using your cellular modem by taking a few key steps, including exposing your cellular IP only when you need to, creating an admin group and having users with strong passwords, locking down the firewall, and using a VPN to restrict access. Check out our Keeping Your Cellular Modem Secure Whitepaper for specific steps you can take to ensure a secure and reliable network.